TERMS TO KNOW
There are a lot of funky names for things in the IT industry! It’s helpful to be familiar with a few common terms that come up frequently when discussing business technology.
- BDR – Backup and Disaster Recovery. Backup is technically a separate process from disaster recovery, but the two often go hand in hand. Backing up to an external hard drive or a cloud service is a common practice to ensure data won’t be lost in a disaster situation.
- -ware (Scareware, malware, adware, spyware, ransomware) All of these are forms of infections, some more malicious than others.
- Adware is the most malign form but still very annoying. It uses some form of advertising delivery and may track your browsing history to tailor content to you.
- Spyware covertly gathers information on how people are using their systems, for example by tracking what you are searching for and websites you visit for ad purposes, or even logging keystrokes to gather passwords and other personal information.
- Ransomware has come to the forefront lately as a popular way to criminals to make quick money. It will generally make your computer unusable, sometimes even encrypting files, and display a screen with instructions on how to pay the attacker to get your computer unlocked. Access to your computer is quite literally ransomed to the perpetrator.
- Scareware is another recently popular way to trick users. You’ll receive a popup with big, bold, scary graphics and language to try and convince you that something is seriously wrong with your computer. It tries to appear legitimate, convincing you that the only way to fix your computer is to use whatever service they’re advertising. Users who believe the scareware will generally end up infecting themselves with even nastier malware and may even be scammed out of money paying for the “fix”.
- Malware is used as a blanket term for many different kinds of infections, and is a combination of the words “malicious” and “software”, hence the broad definition. It includes any hostile and intrusive programs like those above.
- Firewall – A security system that resides on a network to help block attacks and unauthorized traffic. When it is first set up, allowed traffic is defined to the firewall so it knows who to trust. Traffic or requests coming from unknown/unverified sources is denied to protect the network. Computer security borrowed the term from fire prevention, where a firewall is a barrier to prevent fire spreading to other areas.
- Phishing/Pharming/Spoofing – These are all ways to trick you into giving up personal information.
- Phishing is an email that is disguised to look like it’s coming from a trustworthy source. Often these will be from fake banks, businesses, or services and will ask you to confirm sensitive information like your credit card number or password, which will then go straight to the cybercriminal.
- Pharming is a malicious website disguised to look like the original, legitimate site. The perpetrator will set up a replica of a site, and gather unsuspecting users’ login information.
- Spoofing is when a criminal impersonates an individual or organization to attempt to gather personal information. These are those fake calls from the “IRS” or your “bank”, asking you to confirm or update sensitive information.
OUTDATED IT DANGERS
We all know that outdated business technology is annoying – constant computer errors, crashes, waiting minutes for a file to open. But IT that is behind the times can be more severe for a company than inflicting minor irritation and productivity loss.
If you’re still holding on to ancient technology because you don’t think it’s hurting your business, there are plenty of negative effects that may never have crossed your mind.
Hiring
Modern workers have no patience for IT that doesn’t keep up and hinders their productivity (honestly though, who does?)
In fact, a Workforce Study sponsored by Dell and Intel and conducted by Penn Schoen Berland found more than 80% of millennials say workplace tech will influence their job decision. Additionally, 42% would leave a job with unsatisfactory technology. With millennials accounting for an estimated 75% of the workforce by 2025, your business had better get their attention. Showing you value efficiency, innovation, and staying current in your industry via technological adoption is both enticing and in line with their professional goals.
Customer perception
If you walked into a business and saw employees working on yellowed CRT monitors using Windows XP, would you feel comfortable giving them your personal or financial information? Would you think of the company as secure, innovative, and successful? I’m going to guess ‘no’! In today’s technology-centric world, updated systems and processes are some of the most prominent indicators of a strong modern business.
Client perception is a notable factor in how successful companies are. Microsoft surveyed 1,405 consumers about their perception of companies relating to technology in a September 2013 SurveyMonkey poll and found these results:
- 61% think an SMB is outdated if it’s using an operating system that is more than five years old
- 25% think an SMB lacks credibility if it is using a free email service
- 68% think “modern technology” is key to the success of a business
- 70% said they would be “extremely or quite concerned” about providing personal information on an outdated business website
- 91% would stop doing business with a company because of its outdated technology
Ensuring your IT stays up-to-date – current computers and systems; a modern, responsive website; business-class email; and even things like real-time online chat support – creates the perception that your company is successful and on the forefront of innovation.
Valuation and sale
“Businesses equipped with the latest IT environments, such as SaaS platforms and cloud applications to manage their payroll, accounting and other administrative functions can not only attract stronger valuations, but also secure higher sales prices when it comes time to sell” (BizBuySell).
Investors don’t want to get involved with a company that may be obsolete or out of business in five years. They are looking for strong, future-proof organizations that will continue to grow and innovate so they can make money on their investment. As technology grows in business importance, it likewise plays an increasingly large role in initial valuation and eventual sale. Demonstrating that your business is willing and open to adopting new technologies and staying competitive is attractive to investors.
Businesses also must show they value proper cybersecurity – another integral part of modern IT. Data breaches especially, which are becoming more commonplace and advanced, can kill a company. No investor wants to inherit that kind of risk. “Putting the proper cybersecurity in place will protect important data, customer information, while helping to avoid having any unchecked IT risks derail future sale negotiations” (BizBuySell).
Legal and regulatory risks
Releasing new software is not a shady way for companies to squeeze more money out of their customers. Updated programs protect users with the latest safeguards against malware, along with improved functionality. Auditors can fine companies that are late updating or refuse to transition away from unsupported software.
Unsupported software no longer receives updates and patches against new cybersecurity threats, making it a goldmine for hackers to exploit. And when old software does succumb to an infection, there is no longer any developer support.
The risk cost of refusing to update far outweighs the upfront costs of purchasing and learning new software. Maintaining unsupported systems also costs much more than their newer counterparts. And if your business needs to be HIPAA compliant, it is against the law to not use updated, supported software and carries a hefty fine.
Financial and insurance advisors likewise have regulations relating to maintaining current business technology and information.
“Most companies require archiving and approval for all static content displayed on your website. FINRA and the SEC requires archiving for 6 years…Getting fined can be as easy as displaying old, inaccurate information about the market on your website, or promoting a service that may have been good 5 years ago, but today is viewed as a hoax” (AdvisorWebsites).
Environmental impact
As technology improves its environmental footprint decreases. With the modern focus on making everything green, manufacturers develop new products to have less of an impact with each iteration. Technology of the past was not very environmentally friendly, so offices that rely on old tech have a much larger impact than upgraded businesses.
“Data centers and servers are the biggest offenders when it comes to IT inefficiency…Most small server rooms were not designed to operate as server spaces, with configurations that compromise energy efficiency and limit upgrade options, resulting in higher carbon emissions. On average, it has been calculated that a low-range server in the U.S. generates 793 kilograms of carbon dioxide emissions per year” (TriplePundit).
New computers are much more energy-efficient than their older counterparts as well. PC categories like thin clients consume a fraction of the energy traditional, full desktops do. The same holds true for monitors and printers/copiers. Newer models give you more functionality while reducing your office’s environmental footprint.
What happens with electronics after they’re retired is equally important. Proper recycling or re-purposing of devices keeps toxic components from leaking into the water or atmosphere. Many parts and metals from old devices are used in new ones, reducing the need to mine more.
BUSINESS NECESSITIES
It’s rare, if not impossible, for a company to be successful in today’s world without technology. Where 10 years ago you may have been able to get away with just a Hotmail email address, one computer, and store-bought antivirus for your business and you’d be set, times have changed drastically.
To keep your company secure, productive, and compliant, here’s the business technology we recommend.
Business-grade, subscription-based antivirus
Consumer antivirus software generally only covers your basic devices like desktops, laptops, tablets, and phones, and runs separately on each one. Business antivirus, however, is run centrally from your business’ server and protects it as well. An IT admin can monitor and control the protection on each device from one place, and protection is far more robust than in consumer-grade antivirus. In this area, you certainly get what you pay for.
Image-based, automated backup solution (on- and off-site)
Instead of only backing up files, image-based backup creates a copy of your entire operating system and all its data including the system state and application configurations. It’s like a snapshot of your entire computer system. If you ever need to return to a backup, this will ensure it’s restored back to exactly how it was. In addition to having backups, it’s recommended to store them both on- and off-site, for example, both at your location internally and in cloud storage. If something ever happens to the backups stored at your business, for example damage from a fire, flood, theft, or infection, you’ll have these off-site backups as a fail safe. As our CEO likes to say about backups, “two is one, one is none”.
Failover internet
Most businesses run all or a majority of their operations using the internet. If your internet goes down for a period of time, business is forced to come to a halt until it returns. Having a failover means that you have a backup internet connection should something happen to your primary one. “Internet failover is best achieved by having a second Internet service provider (ISP) network as a backup when your primary ISP provider goes down. In the event of such a failure, businesses can manually redirect their IP addresses to the secondary failover network, or automate the failover process.” (Wytec Business)
Managed firewall
A firewall works like a gatekeeper to your business’ network. It blocks unauthorized access while allowing outward traffic. It’s what simultaneously allows you to connect to Google and keeps bad guys from checking out what you’re doing. The difference between a normal firewall and a managed firewall is a normal firewall is configured how you’d like and then perhaps only occasionally updated after that. In a managed firewall, an outside security or IT service monitors your network activity to keep an eye out for security threats or unusual traffic that could pose a threat to your business. This service can also control who in your business can access what sites and services. So if you don’t want your employees visiting YouTube during the workday, you can control it via managed firewall service. This also ties into content filtering (see more below).
Content filtering
Content filtering programs help you control and prevent access to certain things like websites, emails, or programs. This can help keep malware, viruses, hackers, and ransomware from making it into your network. It can also prevent your employees from accessing harmful or time-wasting websites while at work.
Business-class email
If you received an email from a business you hadn’t interacted with before, which would you trust more: business@gmail.com, or support@business.com? Setting up a custom, business-specific email network for your company will both help legitimize it and prevent others from impersonating you.
Network segmentation
“Network segmentation is the process of splitting your network into different ‘segments’ or ‘subnetworks’. This matters because, by default, when you connect a bunch of devices to the same network, they can all talk to each other and potentially listen in on each others’ network traffic without any sort of monitoring or rules in place…once you start adding devices that [you] might not trust so much—guests’ devices, older legacy computers or servers that you can’t replace for some reason, and even otherwise trusted employee’s personal phones and computers—that gets a lot more problematic.
So, that’s where network segmentation comes in. Segmenting your network allows you to put different people or sets of hardware on different network segments with rules about how one segment can talk to the others. Network segments are often designed around how much we trust the users or devices in question. Think about things like putting guest users on one segment, very sensitive data like accounting systems on another segment of its own, etc.” (IT Freedom)
Multi-pronged security
In cohesion with all of the above, we feel a robust, multi-faceted security plan is the most important element for the modern business.
The most successful business with great clients, culture, profitability, and growth can be absolutely crippled in just hours if they’re hit by a cyberattack or data breach.
We find that a lot of people have the attitude of “it hasn’t happened to me yet, so I’m not going to worry about it”. PLEASE take your security seriously. Ransomware, breaches, phishing, and attacks are on the rise, and criminals know that smaller firms especially tend to have less security resources, making them easy targets.
[Snag our Business Guide to Cybersecurity to help you get secure.]
It’s so easy to prevent something major from ever happening in the first place with a solid security and backup plan. If you haven’t put something into place yet, do it ASAP. It’s never too late.
If you know you need to do more but don’t know where to start, that’s okay! Contact us or any other reputable IT support provider who will be happy to help you.
IT SPEND & BUDGETING
We’ve seen that business leaders often avoid investing in new technology as they’re scared of the cost. The great thing, though, is that technology improves every year and once-expensive items get much more affordable.
Along with tech improvements, IT’s function in business has shifted dramatically. Savvy executives have realized that harnessing the power of modern technology can help accomplish overall business goals and drive growth, efficiency, customer and employee satisfaction, and profit.
Some gains that come from well-invested IT dollars are:
- The ability to reach more potential customers and develop a better business relationship with your consumer base
- Providing better and unique service to customers
- Supporting better relationships with key partners
- Using customer demand to better guide the business
- Streamlining operations, reducing costs, improving efficiency, maximizing profit, minimizing waste, devoting talent to core business instead of overhead
- Rising above competitors to establish your business as the most progressive and forward-thinking in the industry
Customer expectations are rising quickly and the bar is always climbing; technology allows your business to compete and rise above in this digital world.
We encourage you to think of all the ways IT can help your business succeed, rather than viewing it as just another expense.
Industry averages
On average, businesses spend between 3-6% of their revenue on IT.
Company size generally has a large effect on budget size, and should be taken into consideration when planning your fund allocation. Small and medium businesses surprisingly often outspend larger ones when it comes to their IT budget (SearchCIO.techtarget.com):
- The average small company (less than $50 million in revenue) spends 6.9% of their revenue on IT
- Mid-sized (between $50 million – $2 billion) spend 4.1%
- Larger companies (over $2 billion) spend a relatively tiny 3.2%
As technology becomes a greater part of business operations, budgets have been steadily growing.
Industry also seems to have a noticeable effect on IT spend. This makes sense as some rely much more heavily on technology. Here is a breakdown of IT budget as a percentage of revenue broken down by industry, courtesy of Deloitte.
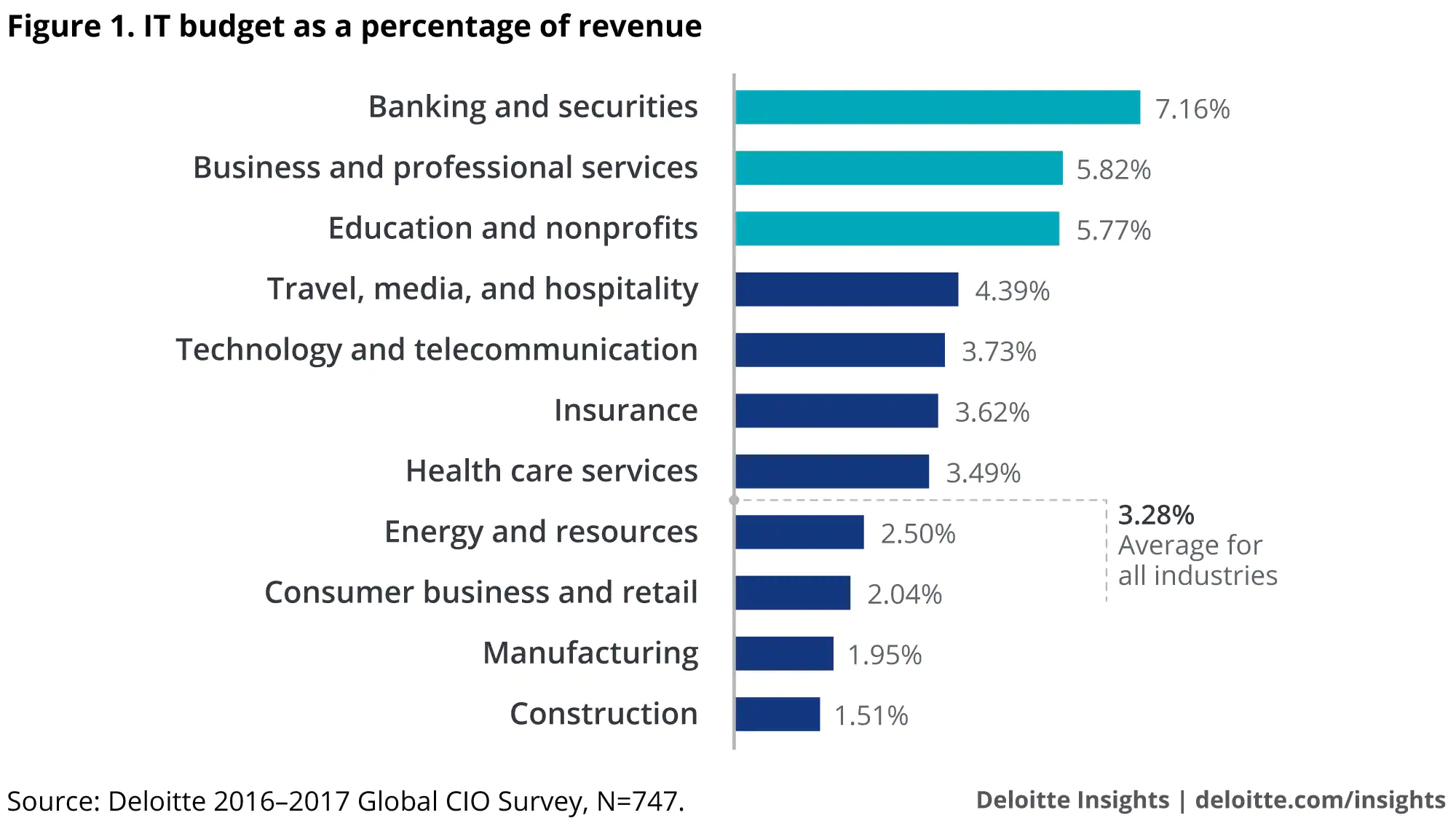
It’s important to note that the companies that invest the most in IT aren’t necessarily the best performers. On average, the most successful small and medium companies are more frugal when it comes to IT spending (as long as they do it judiciously). Regardless of amount of spending, if investments aren’t made and used wisely, it will be reflected in that company’s returns and productivity.
In order to produce a reliable technology budget, it’s critical that a company go through an assessment phase to review the network and its related systems from several angles (users, hardware, and current IT vendors). Finding a trusted IT consulting firm to guide this process is ideal, as it allows for an unbiased, all-inclusive assessment, along with sound budgeting advice that’s in line with the overall business objectives.
The 3-6% average is a great guideline, but the final number will depend on your company’s individual needs and goals.
Budgeting assessment questions
There are a few questions every business owner should consider when determining their IT budget to effectively implement technology decisions (McKinsey.com). A few crucial points are:
How will IT change the basis of competition in our industry?
“For incumbents in many sectors, technology is becoming an arms race. Companies are harnessing technologies such as social media and location-based services to reinvent the customer experience and capture market share.” It is important to know who your emerging or existing competitors are, how they are taking advantage of technology, and how your IT is helping you win against them and even enter new markets.
What will it take to exceed our customers’ expectations in a digital world?
Companies who are e-commerce leaders like Amazon and Apple are re-educating customers as to what the online business world can be. Ultra-convenient and personalized experiences are pushing customer expectations higher and upping demand for consumer-driven technology. You should understand how your customer experience compares with that of leaders in other sectors, what your customers expect and what it will take to delight them, and have clear plans for how to meet or exceed their expectations.
Do our business plans reflect the full potential of technology to improve our business?
“Technology expenses can be high, but they are relatively small compared with their potential to boost the operating performance of a business.” Technology can drive revenues, reduce overall costs, and lower risk. By seizing opportunities and mitigating threats, companies can dramatically improve their performance in all sectors. Ultimately, the strategy that emerges from an assessment of opportunities and threats should be an integrated plan that shows how the business will beat the competition using information technology over many years to come, not simply a revised annual IT budget.
How will IT improve our operational and strategic agility?
Leading companies are continually using IT to improve business agility and streamline processes. IT agility can be increased by changing the systems landscape, improving data quality, optimizing IT delivery processes, and building flexibility into the company. To be a leader, your company must measure and manage both business and IT agility, ensuring that the organization can operate competitively and determining where improvements can be made.
Do we have the capabilities required to deliver value from IT?
It is one thing to have IT, and another thing entirely to use it effectively. “Technology alone delivers no value. It is the combination of a clear strategy, the right technology, high-quality data, appropriate skills, and lean processes that adds up to create value.” Leading organizations actively assess their capabilities in these dimensions and target any weak spots to ensure they will derive value from IT changes.
Are we comfortable with our level of IT risk?
“Cybersecurity is a significant and growing IT issue. Every large company’s security has been breached, and most executives have a poor understanding of the risks.” Companies need a comprehensive system for managing IT risk that assesses the full range of threats and addresses their root causes. It is important with any IT budget strategy to ensure you are mitigating risks and preventing security breaches as comprehensively as possible.
[Get our full IT budgeting guide for more help in this area.]
SUPPORTING YOUR IT
Over 45% of SMBs have no dedicated in-house IT staff and no contracted IT consultant regularly monitoring and managing their technology.
Roughly only 7% of SMBs have a full-time onsite IT technician on payroll.
The rest rely on third-party on-call IT companies who appear only when technology goes haywire and disrupts business. These on-call companies sometimes take a day or two to even show up, which means issues aren’t resolved in a timely and efficient manner. And did we mention they’re expensive?
Most SMBs say they simply can’t afford full-time in-house support. Even those who do budget for it face overwhelming challenges. They often experience a revolving door of on-site help who leave for a larger company and better salary once they’ve beefed up their resume. And those hires that do remain loyal often feel as if they have no reliable help and become overworked and frazzled as the business and their responsibilities grow. Discontent may even set in if wages aren’t raised proportionately to the added responsibilities, or if they grow bored of doing the same mundane, repetitive work everyday.
But today’s SMB has access to technology that won’t drain resources. In particular, the evolution of cloud computing and managed services can either automate or re-assign a lot of the day-to-day caretaking of technology to remote employees, leaving on-site support available for more meaningful and potentially profitable projects.
Should you hire someone in-house, outsource your IT, or both?
It’s difficult to give a 100% certain answer to this question. It will depend a lot on your current business operations, your needs, your preferences, and your future plans. We’ve worked with many companies trying to make this decision, so hopefully our experience can help make it a little easier.
When to hire in-house
Generally, hiring someone internally will cost more than outsourcing/hiring a managed IT service company. You’re looking at easily a $50k+ salary, benefits, vacation and paid time off, onboarding time and costs, and then costs to off-board and rehire should that person leave your company.
The pros of shouldering the extra cost include being able to manage and direct their work and having someone who is extremely familiar with your business, its team, and your goals.
If you’re a big proponent of control, team cohesiveness, and keeping as much as possible in-house, then you’ll likely want to look at hiring into your team. If your business doesn’t require much in the way of technology and hiring an entire outside company to take care of it doesn’t make sense, hiring someone in-house could be suitable. If you picture this role handling more than technology or cross-training, you’ll probably want to hire in-house.
When to outsource
Outsourcing can range from the typical “IT guy” persona who comes by to fix things when they break, to a managed IT service company that is responsible for your entire infrastructure 24/7.
While the break-fix method works for some companies, we don’t recommend it. We’ve been there and we moved into managed services for a reason. Most companies are dependent on their technology working, otherwise business comes to a halt, and few can afford that risk.
Managed IT service ensures that potential issues are spotted and mitigated before they affect business, and puts your IT provider on the same page as your company. It moves things from a vendor relationship to a business partnership. Obviously, we’re big fans, but we’ll refrain from going on forever! You can read more about managed service here if it sounds like a good option for your business.
As far as when IT outsourcing makes more sense, there are a lot of factors to consider. If your technology fails, can you continue to operate? Do you need or want access to support 24/7? How long can you afford to be down if something happens? Do you need expertise in a wide array of IT specializations? Do you not have the time or resources to train and manage someone in-house?
Managed IT service gives you access to a team of IT people with expertise in varied areas; a consulting relationship that will help you match business goals with technology solutions; 24/7/365 proactive support and management; visibility and analytics about your infrastructure; and full coverage over business-critical areas like security, backup, disaster recovery, continuity, compliance, data management, and IT projects. And often this comes for less than hiring someone in-house.
While it’s still not a fit for every business, managed IT is becoming more and more popular and accessible to all kinds of organizations.
When to do both
If you can’t decide, or if you want the best of both worlds, combining in-house and outsourced talent is a solid choice. You have the benefit of an internal team that is deeply integrated into your company and culture, and an outside team that can easily fill in any gaps.
Often, in-house teams’ daily work consists of menial tasks like changing passwords and troubleshooting computer issues. Not many techs love doing this! They would much rather focus on helping you work towards business goals like improving operations, facilitating growth, increasing profits, and boosting customer and employee satisfaction. This can all be done with technology, but only if your IT team has the time to design and implement solutions.
This is the perfect scenario for a third-party IT company to come in and assist. They can unload the burden of repetitive maintenance tasks from your team and allow them to work on high-level projects that are more interesting. And when needed, the outside IT company can offer their advice and expertise to your team.
This can end up being the most expensive option, but if it makes sense for your company, it’s a great investment.
ESTABLISHING GUIDELINES
As you’re implementing or updating your company’s technology plans, it’s the perfect time to work on your acceptable use policy.
An acceptable use policy establishes rules for using the company network and devices. This will protect your business from dangerous behavior plus hold offenders accountable.
“While an AUP helps educate employees on issues such as password protection and online security, it also serves an important legal function for the company. In the event that an employee uses a company’s network for unsanctioned personal activities, having an AUP in place can help prevent (or reduce) any legal issues that may arise…” (cnbwaco.com)
Follow along to create a robust acceptable use policy for business.
Outline sections
What are the six key elements of an AUP? We recommend every policy include these sections:
- Overview – a high-level description of the document’s purpose and key takeaways
- Definitions – define any terms that may be confused, and explain words or phrases unique to your business
- Scope – what the policy does and does not cover and what situations it applies to
- Policies – the “meat” of the document, in sections that cover use and behavior for each category
- Enforcement – consequences for failing to adhere to standards, and how employees will be held accountable
- Revisions and tracking – create a schedule to revisit the document and be sure to track any changes.
Make things easier with an acceptable use policy template
Writing an acceptable use policy from scratch is very time-consuming and, frankly, unnecessary nowadays. Why not get a head start with a template? You can find plenty for free online.
Here are some acceptable use policy examples and templates to explore:
Sample Internet Acceptable Use Policy by PearlSoftware
Sample Internet Usage Policy by GFI Software
Sample Acceptable Use Policy via SpiceWorks (includes verbiage for HIPAA-compliant businesses)
Sample Acceptable Use Policy for Schools from TeacherVision
Computer Use Policy Template from Association of Corporate Counsel
Acceptable Use Policy Template for Business by Get Safe Online
Customize to your company needs
If you’re using a template, decide what applies to your company and what should change. Even if starting from scratch, consider these integral points:
Internet use
Which websites should be prohibited during work hours? Many are obvious, such as pornography or gambling, but what about Spotify or news websites? Do certain people, such as your marketing team, need access to social media while others don’t? Don’t forget to outline acceptable behavior for sites like these that have potential for abuse.
Some common restricted websites are:
- Social media (Facebook, Twitter, Pinterest, Instagram, Tumblr, Reddit, Flickr)
- Streaming video/music websites (YouTube, Vimeo, Vevo, Twitch, Pandora, Spotify)
- Job-hunting sites (Indeed, Monster, Craigslist, ZipRecruiter, Snagajob)
- Shopping (eBay, Amazon, Alibaba, Etsy, Overstock)
- News (MSN, Yahoo, TIME, USA Today, New York Times, Washington Post, Huffington Post, CNN, Fox, NBC, BuzzFeed, Upworthy, Distractify)
- Personal email (Gmail, Yahoo, Hotmail, AOL)
- All porn, gambling, and illegal activity websites
Every company varies in its views on blocked websites. Most will use a mix of these and other sites. Decide what works for your business, and update it as needed.
Security
Another important consideration is security. Outline best practices that employees should follow when using company devices.
Here are a few of our security policy recommendations:
- Never allow use of public WiFi on company devices
- Employees should never share passwords, and change theirs often (at least once a month). Be sure to define standards for acceptable, secure passwords too.
- Create a schedule for antivirus, anti-malware, and company software updates
- Employees should never open email attachments or links they aren’t expecting. If a suspicious email is received, who should employees send it to for review?
- Consider requiring two-factor authentication for programs and apps that support it
- Unless used for business purposes, we recommend disallowing use of social media on company devices. Many instances of malware and phishing happen through social media.
Each company has different security needs – make sure yours are thoroughly defined and cover all networks and devices.
Don’t forget to include physical security policies. How should company devices be secured, stored, and transported?
Confidential data
Your business likely holds a large amount of both confidential and proprietary data. Client, employee, product, service, and other business details are important to handle correctly.
You need to start by figuring out what this confidential data is in your business. From there, explain proper standards for accessing, sharing, storing, and handling this information.
Incident response
Don’t forget about this important section! No company is 100% airtight. Should something happen, what is your response plan? Who needs to be notified and what departments are involved in recovery?
We highly recommend including that employees will not be retaliated against for notifying management of a potential security incident. If something has happened, it will be a problem whether the employee tries to hide it or not. Everyone makes mistakes. And you will have a better chance of quick recovery if you know about the incident sooner rather than later. Note that a mistake is far different from malicious intent and should be treated as such. Intentional violations should, of course, not be protected (but then again, we doubt bad actors would notify you anyway!)
Guest access
Does your company offer guest WiFi/internet access? If so, you’ll want to define standards and secure policies for guest access. This may cover customers, vendors, or partners visiting your place of business.
We recommend creating a guest network for this purpose. This will ensure guests only have access to what they need, and not your company’s internal network and files.
Email is an essential tool for every modern business. Its proper use for your company needs to be clear. Are your employees allowed to use their work email for personal needs? What are proper business communication standards, both internally and externally?
We recommend including a general best use section as well. Some employees may not be aware of the many threats that come through email – phishing, scams, spoofing, malware/viruses. Take the time to educate your team on how to spot, avoid, and handle potential threats.
Decide on AUP enforcement and violation standards
This section is important to review in your template. What works for one company may not be appropriate for yours. Some companies revoke internet access for repeat offenders. But this may be impossible in your business.
We recommend working with your managerial or executive team to define acceptable consequences. Take into consideration the varying severity of different violations. And ensure that you have the ability to act on these policies. Without standardized enforcement, your AUP won’t be taken seriously.
Review your acceptable use policy with HR, legal, and internal teams
Before introducing your AUP to staff, you’ll want to review it with human resources and your lawyer. This will ensure you’re not overstepping any boundaries, or breaking employment or state/federal laws.
It’s also a good idea to get feedback from both managers and employees at every level. They may point out items that were forgotten or provide better ideas for certain policies. While it’s important to protect your company’s assets, it’s equally important to keep your team productive. If a person can’t do their job well because of something in your AUP, that’s a problem.
Also be sure that policies are well explained. No one likes following rules that they don’t see a point to. Explaining the reasoning behind certain standards can help employees understand policies they may have initially disagreed with.
When your acceptable use policy has been reviewed, approved, and distributed – have every staff member sign a copy of the document. In the event a policy is broken, you can hold the offender accountable.
Create and maintain an update schedule
Your AUP is a living, changing document. Revisit it on at least a yearly basis to determine if policies are still relevant and accurate.
Be sure to include revision tracking to follow any changes made. And don’t forget to have staff sign the new acceptable use policy as it’s updated.
WRAPPING UP
We hope this helps you feel more comfortable and confident in creating an IT business plan that drives your company towards its goals.
There is a ton of information contained in this guide and we know that it can be overwhelming, especially if you’re trying to handle everything yourself.
If you’d like some help, we would love to hear from you. Even if we may not be the best fit to work together, we can refer you to reputable IT providers in just about every state. Finding someone you trust to help you with your business technology plan is ideal and will make things much easier and less stressful (and who doesn’t want hitting their goals to be easier?)
Cheers to you and your success!




