New cybersecurity threats like phishing attacks, ransomware, and scams are always popping up. Stay up to date on the latest widespread threats and protection methods in our recurring series.
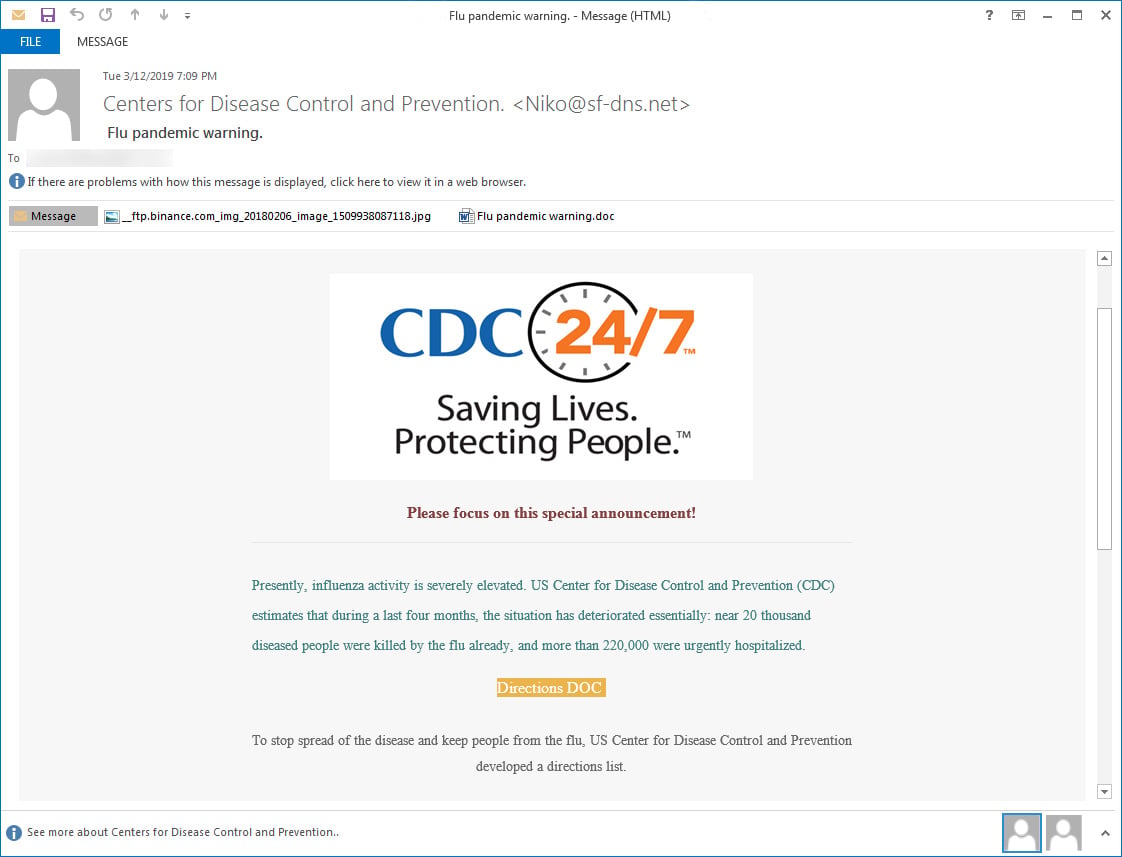
FAKE CENTERS FOR DISEASE CONTROL AND PREVENTION (CDC) EMAILS SPREADING RANSOMWARE
Scammers are impersonating the CDC organization and sending emails with a subject line of “Flu pandemic warning”. The emails attempt to get the reader to open an attachment detailing the “pandemic” and how to stop its spread.
Opening the attachment will prompt the recipient to Enable Editing and Enable Content in order to view it. If all that happens, then a malicious file will be executed installing GandCrab v5.2 ransomware on the victim computer.
What to do: If you receive this email, it’s definitely a fake! We recommend never opening an email attachment unless you know without a doubt who sent it, and you were expecting it. Malware and viruses are commonly spread through email attachments so always be aware.
MALWARE SPREADING THROUGH FAKE ASUS SECURITY UPDATE
:origin()/pre00/d057/th/pre/i/2014/262/9/c/asus_wallpaper_1920_x_1080_by_pgene-d7zsceh.jpg)
A hacker group called ShadowHammer was able to distribute malware through a fake security update to as many as one million Asus computers.
“Asus does say it’s taken steps to ensure such a trojan horse won’t make it through again, including ‘multiple security verification mechanisms to prevent any malicious manipulation’ and ‘an enhanced end-to-end encryption mechanism.’
‘At the same time, we have also updated and strengthened our server-to-end-user software architecture to prevent similar attacks from happening in the future,’ Asus says.” (The Verge)
What to do: Asus has released a (real) security patch to fix the malware and keep the phony update away from your computer. If you were affected by this, you can download the update from their Live Update software tool.
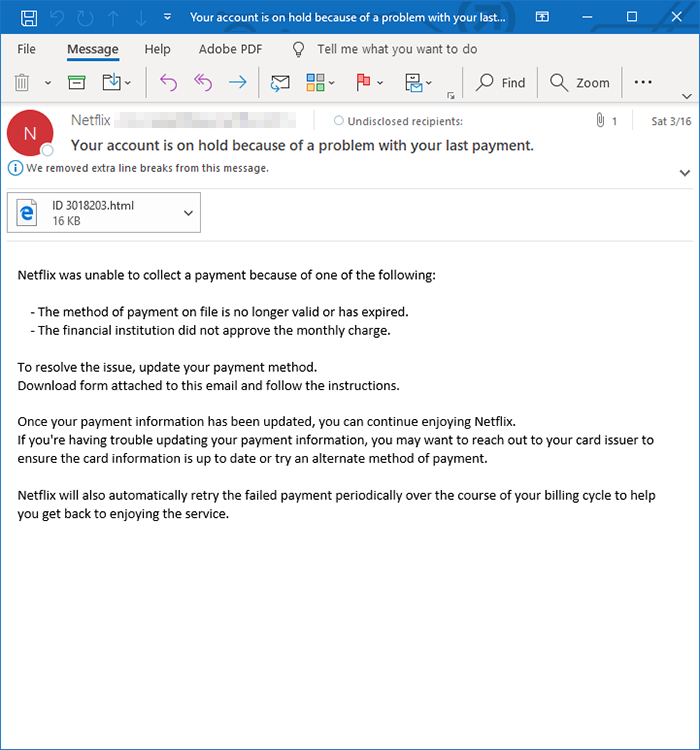
PHISHING CAMPAIGN TARGETING NETFLIX AND AMEX CUSTOMERS
Cybercriminals are targeting Netflix and American Express customers through emails stating that their account is on hold due to payment issues. Clicking the link to resolve this issue in the email leads to a well-crafted, but fake, payment form. Filling this out will of course give your sensitive information to the criminals.
What to do: If you have received this email or suspect your information has been taken, get in touch with the proper support. If your information has been stolen, alert your bank and cancel any possibly affected cards. If you’ve receive this or a similar email, open a support ticket with Netflix or AmEx. Make sure to start a new email chain for this and don’t simply reply to the email in question!
MYPILLOW AND AMERISLEEP DATA BREACH

“After being targeted as early as 2017, both online retailers faced card skimming attacks. In this scheme, hackers will insert malicious code into website checkout pages and covertly swipe customer payment information.
Although MyPillow discovered the first compromise almost immediately, it argued that the second attack did not result in the loss of information. On the other hand, Amerisleep has not responded to comments.
Depending on what further investigations reveal, it is possible that the sleep companies will face hefty fines for their delay in responding as well as scrutiny from online shoppers.” (ID Agent)
What to do: If you’ve purchased anything from either site, we recommend contacting the bank that issued the card(s) you used to make purchases. Review your credit report and ensure there are no fraudulent charges.
SECURITY FLAWS WITH MEDTRONIC CARDIAC IMPLANTABLE DEFIBRILLATORS
“The FDA’s March 21 security alert warned caregivers and patients who use Medtronic cardiac implantable cardioverter defibrillators (ICDs) or cardiac resynchronization therapy defibrillators (CRT-Ds) to treat patients with heart failure or rhythm problems that a critical security vulnerability in the devices exists because they do not use encryption, authentication or authorization.
‘The FDA has confirmed that these vulnerabilities, if exploited, could allow an unauthorized individual (for example, someone other than the patient’s physician) to access and potentially manipulate an implantable device, home monitor, or clinic programmer.’
If the vulnerabilities were exploited, criminals could use radio communications to take control of the medical devices while the devices are inside a person.” (Infosecurity Magazine)
What to do: There isn’t much that can be done in this situation. Patients who receive implants generally don’t get to shop around or choose which brand they receive. Surgery to replace a device that is inside of you comes with its own risks. If you are concerned about yourself or someone else with this implant, get in touch with the FDA or your doctor for advice on how to handle the situation.
![]() If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!
If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!