New cybersecurity threats like phishing attacks, ransomware, and scams are always popping up. Stay up to date on the latest widespread threats and protection methods in our recurring series.
FAKE BOMB THREAT EMAIL SCAM
On a Thursday in December, offices across the country received an email threat: pay the sender $20,000 in Bitcoin or they would detonate a bomb that they planted in the building. This caused hundreds of evacuations and police investigations, but no bombs were ever found.
Luckily this seems to have been an ineffective way for the scammers to make money as they received hardly any money. However, they were able to cause panic, disrupt workdays, and waste police resources.
What to do: There isn’t much to do at this point! The FBI is investigating the source of these emails and it seems to have been a short-lived attempt. If you receive any suspicious emails that resemble this scam, report it to your IT team.
FACEBOOK USER PHOTO BREACH
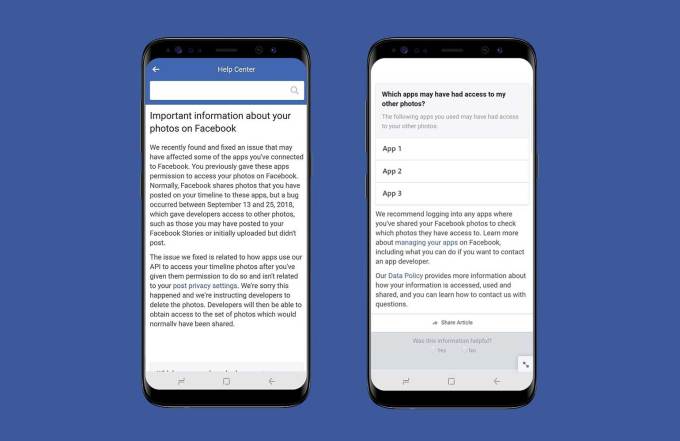
Facebook reported on December 14th that a bug had granted third-party apps permission to users’ photos. Normally when a user grants photograph permissions to an app, it should only have access to the users’ publicly shared timeline photos. This bug allowed access to private images and those shared in other places like the Marketplace or Stories.
It’s estimated the bug has affected up to 6.8 million users and 1,500 apps. It has been fixed since being discovered.
What to do: If you were affected, you will have received a Facebook message letting you know. There is nothing you should or really can do to help here. Facebook is working with the third-parties to ensure any accessed photos are deleted. If you are still concerned, it’s worthwhile to go through Facebook’s privacy settings to check how much you’re sharing and who has access to your data.
QUORA DATA BREACH
In early December, Quora revealed a data breach that gave hackers access to the personal data of an estimated 100 million users. The information includes names, email addresses, encrypted passwords, Quora activity, and data from social networks like Facebook and Twitter if people linked them to their Quora accounts.
Since the breach, Quora has notified its users and taken steps to secure the platform.
What to do: If you were affected, you would have gotten a message from Quora and been logged out of your account. We recommend changing your account password either way, and changing any other accounts you have that use the same password.
APPLE ID PHISHING WITH FAKE APP STORE RECEIPTS
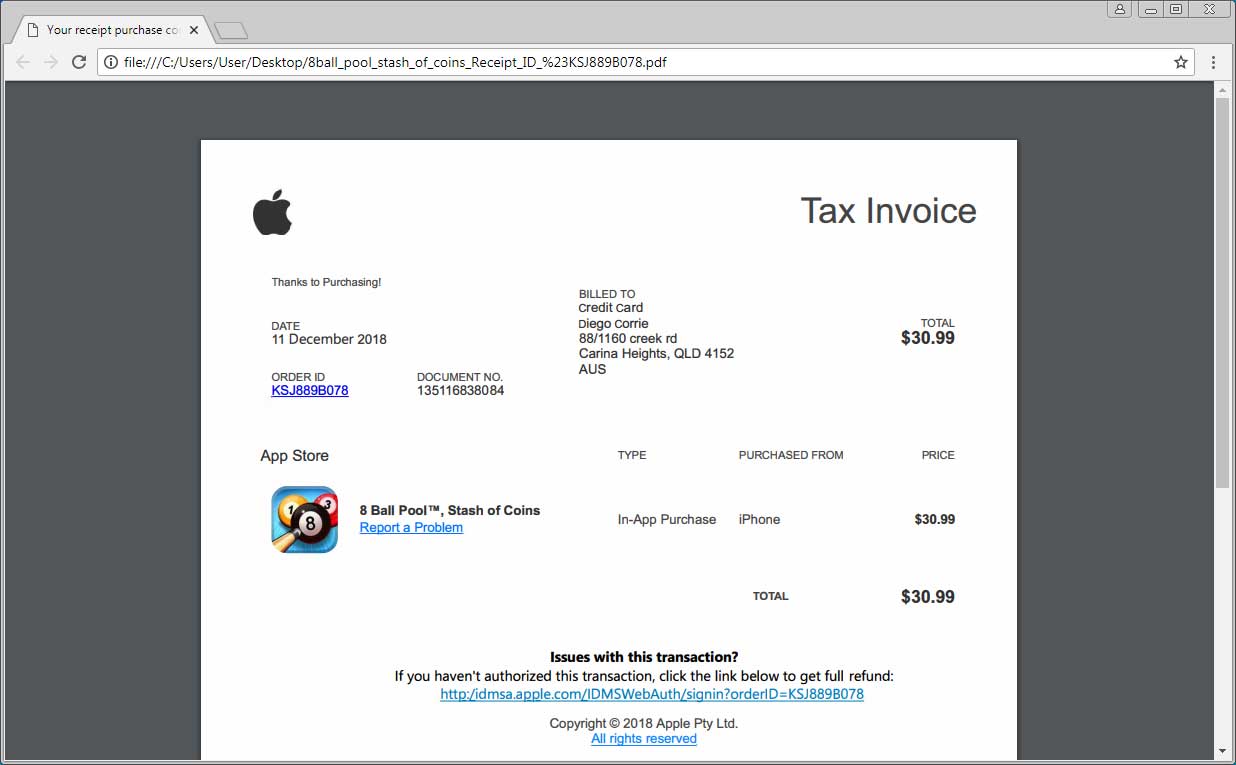
This scam comes in the form of an email telling you that a purchase was made under your account from the Apple App store. The email will have a PDF attached as a “receipt”. Interestingly, the PDF itself does not install malware. Upon opening it, the recipient will be shown what appears to be a legitimate invoice detailing the purchase with links inside to dispute it.
Clicking the links will lead to a fake Apple page where you will be prompted to recover your account (which has been “locked for security reasons”) by entering all your account and personal information, including your name, address, DOB, payment information, and security questions. After this you will be redirected back to the real Apple homepage and the scammer has all your important information.
What to do: As always, be extremely cautious of any emails that contain attachments. If you did not make a purchase and receive an email like this, do not open the attachment or click any links in the email. Instead call the company directly and ask about the situation. They will be able to tell you if it’s real or a fraud. If you do accidentally click on a link, you’ll likely notice that the website address/URL you’re taken to is not an Apple domain – always keep an eye out for clues like this.
INTERNET EXPLORER FLAW AND EMERGENCY PATCH

Microsoft has released an emergency patch after discovering a flaw that could allow an attacker to gain the same user rights as the current user. Being that most use their computer as an administrator which allows full computer access and modification, this could be very dangerous for victims.
“The vulnerability affects Internet Explorer 11 from Windows 7 to Windows 10 as well as Windows Server 2012, 2016 and 2019. Internet Explorer 9 is affected on Windows Server 2008, while Internet Explorer 10 is affected on Windows Server 2012” stated Satnam Narang, senior research engineer at Tenable.
What to do: The flaw is being actively used by attackers, so users should install updates as soon as possible on their computers. Criminals are gaining access to systems using this bug by sending users to fake websites through phishing emails, so be extra wary of emails you receive as well and never click suspicious links.
![]() If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!
If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!



