New cybersecurity threats like phishing attacks, ransomware, and scams are always popping up. Stay up to date on the latest widespread threats and protection methods in our recurring series.
APPLE SPOOFED PHONE CALL PHISHING SCAM
Scammers are using caller ID/phone number spoofing to trick Apple users into giving them personal and financial information. Phone number spoofing is when someone uses VoIP technology and special software that allows them to impersonate another caller. Their phone number will display on your end as whatever phone number they want, not the number they are actually calling from. This is a huge problem that you’ve probably already experienced.
In their campaign, the scammers are using this tactic to call Apple consumers from Apple’s actual phone number. Because of Apple’s old MobileMe service, people who have been using Apple’s devices since before 2011 will automatically have Apple’s contact information stored in their phone. This causes the spoofed calls to display Apple’s logo, address, and phone number, making the scam even more dubious.
These calls try to convince recipients that Apple is calling to alert them about a data breach. They supply a phone number to call back that leads to phony “Apple support”, where they then try to get you to hand over your personal information, banking details, and even remote control of your computer.
What to do: If you receive an unsolicited call that purports to be from Apple and requests you give out personal information, do not give it! Companies have policies that specifically forbid them from asking about your personal details over calls or texts for this reason. Apple in particular does not make unsolicited support phone calls, and will never initiate something like this. If you have gotten one of these calls and gave out your information, alert Apple support immediately and any companies whose information you shared (banking, other financial, personal accounts).
PAYPAL PHISHING AD SCAM
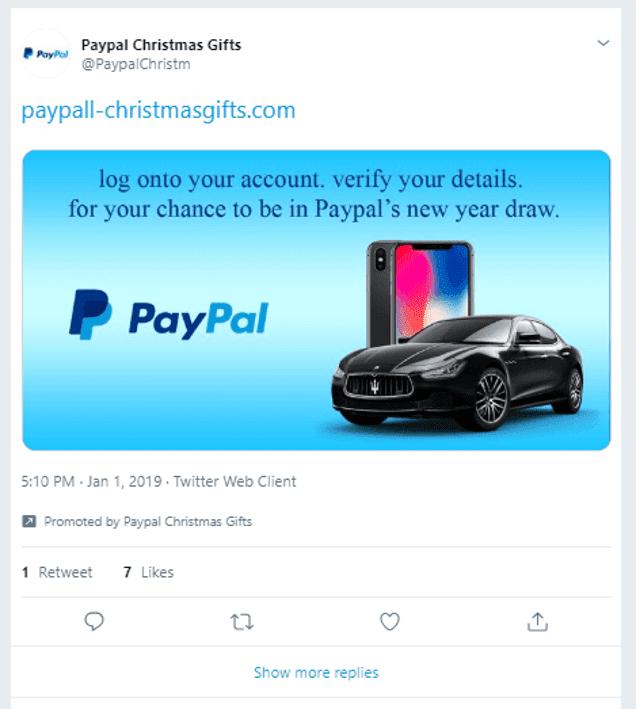
Via Matthew Hughes from The Next Web
In December 2018/January 2019 an account posing as Paypal posted an advertisement on Twitter attempting to bait users into giving the creator their personal and financial details.
The promoted tweet from @PaypalChristm had a few obvious red flags to those familiar with these scams but could have easily been mistaken as legitimate to others. The tweet promoted a fake “end of the year giveaway”. After clicking, users were taken to a phony Paypal login page, and if credentials were entered then led to a page prompting you to enter credit card details.
The tweet was promoted for about 30 minutes before being flagged and removed and the account suspended.
What to do: If you clicked this ad and gave any of your information, contact Paypal and your banks immediately to alert them. Keep an eye on your accounts and report any unusual activity. Always be wary of promotions like these that seem fishy or too good to be true, and that ask for unusual information.
MILLIONS OF FINANCIAL DOCUMENTS LEAKED ONLINE
More than 24 million sensitive documents containing the personal information of people who have applied for loans and mortgages from US banks were found leaked online after a server security lapse. The server that the documents were stored on was found to be unsecured and available for anyone to view for about two weeks and contained over 10 years of data.
TechCrunch reported that they traced the leak “back to Ascension, a data and analytics company for the financial industry, based in Fort Worth, Texas. The company provides data analysis and portfolio valuations. Among its services, the Ascension converts paper documents and handwritten notes into computer-readable files — known as OCR.”
Ascension blamed the leak on mismanagement of the data by a vendor called OpticsML.
“From our review, it was clear that the documents pertain to loans and mortgages and other correspondence from several of the major financial and lending institutions dating as far back as 2008, if not longer, including CitiFinancial, a now-defunct lending finance arm of Citigroup, files from HSBC Life Insurance, Wells Fargo, CapitalOne and some U.S. federal departments, including the Department of Housing and Urban Development.
Some of the companies have long been defunct, after selling their mortgage divisions and assets to other companies.
Though not all files contained the highly sensitive and personal data points, we found: names, addresses, birth dates, Social Security numbers, and bank and checking account numbers, as well as details of loan agreements that include sensitive financial information, such as why the person is requesting the loan.
Some of the documents also note if a person has filed for bankruptcy and tax documents, including annual W-2 tax forms, which are targets for scammers to claim false refunds.” (TechCrunch)
What to do: If you have applied for a mortgage or loan with a US bank in the last decade, we recommend monitoring your credit report and accounts for any unusual activity. The exposed information has been taken down and companies are staying alert to any use of the data, but you will be the first line of defense.
MASSIVE DATA BREACH CONTAINING OVER ONE MILLION EMAILS AND PASSWORDS
One of the largest data breaches in history was discovered and contains about 773 million email addresses and 21 million passwords, dubbed Collection #1. It is made up of the information collected from several large data breaches within the last few years.
This information can be used by hackers, who will try combinations of emails and passwords from troves like this to try and access your online accounts. They rely on people recycling passwords on separate accounts which most are guilty of doing.
What to do: You can use websites like haveibeenpwned.com to check if your email address is found as stolen in this or any other breach. If you do discover your email address is listed, we recommend changing your password immediately as most times passwords are taken along with email addresses. If you use your email password as a password on any of your other accounts, change those immediately as well. And we highly recommend never reusing passwords on two or more accounts.
VOICEMAIL PHISHING CAMPAIGN
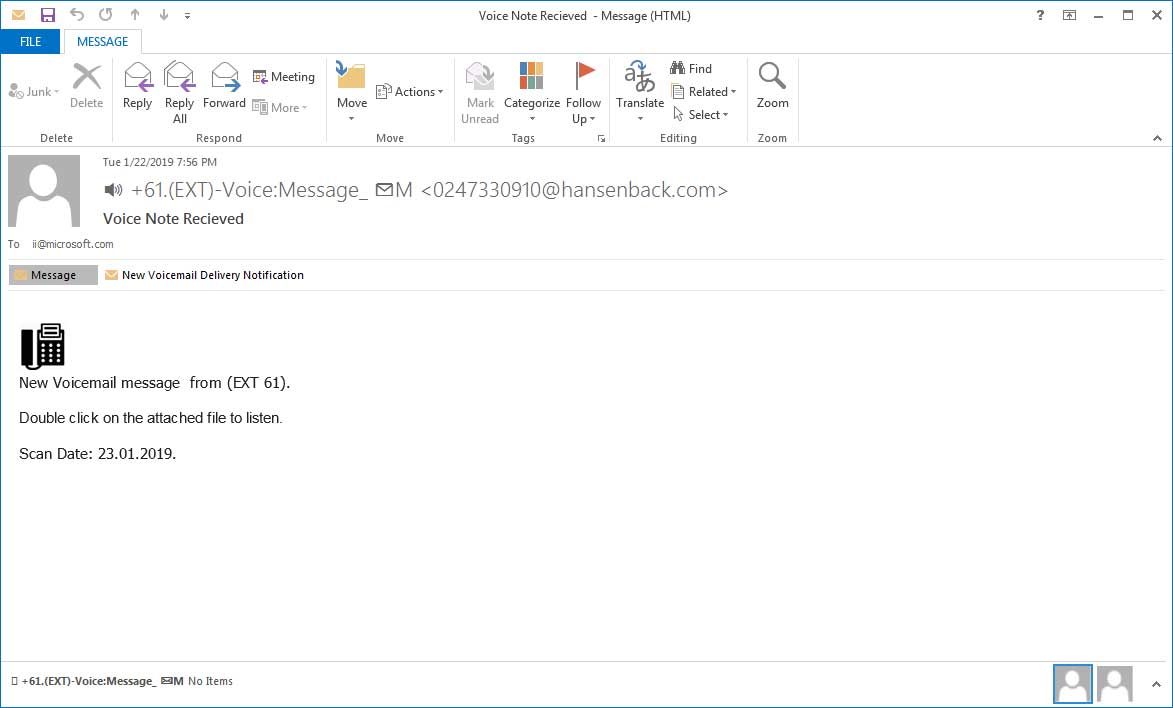
This campaign uses email attachments to try to convince recipients that they have received a voicemail. If you have ever used a program like this in your office, you’ll be familiar with receiving voicemails as email messages and attachments.
This bogus message comes in with a vague message that you have received a voicemail and asks you to open the attachment to listen to it. Clicking the link will take you to a phishing site that pretends to be a Microsoft login page. Something unique about this campaign is that no matter what password is entered, even if correct, it will tell you that the password was incorrect and to re-enter it. This seems to be to confirm your password for the hackers.
If all these steps are completed, you’ll be taken to an mp3 recording of a voicemail. It is quite vague and doesn’t contain a callback number that could be used to verify the message, likely causing most people to write it off as a wrong number, but adding legitimacy to the scam.
You can view the fake pages and listen to the voicemail recording on BleepingComputer.com
What to do: Be cautious when opening any email attachments. If the message looks unusual or different from other voicemail notifications (or you don’t even use this service at all), then do not open it. Report any suspicious messages to your IT team who can confirm them for you. If you have given your information away, change your password and contact Microsoft support.
If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!



