The New Zealand writer Robert Black once said, “Show me the asset, and I’ll show you its price.” There is truth to what he said – assets are the backbone of any organization. Assets need to be protected and that protection must include both digital and physical assets
For the purpose of this article, digital assets will be defined as any device, equipment, or other component that has digitally stored content. Typical examples include company-related images, photos and graphics, videos, audio files and recordings, HTML documents (and associated files, such as CSS), text files/documents, spreadsheets, and slide decks/presentations.
Investopedia defines a physical asset as “an item of economic, commercial, or exchange value that has a material existence”. There are many examples of physical assets, including land/property, buildings, machinery, equipment, tools, vehicles, or any other form of economic resource that is tangible.
Importantly, both classes of assets have intrinsic value, whether market-based or other value to the organization.
KEY DIFFERENCES BETWEEN PROTECTING DIGITAL & PHYSICAL ASSETS
There are important differences between how a company protects its physical assets compared to its digital assets, arising mostly due to the nature of the two asset classes and what they represent for an organization:
Different focuses
The focus for digital assets is primarily external since most threats to digital content arise from adversaries outside an organization. Hacking of digital equipment or databases can be done from within, of course, but is primarily an external threat. This makes protecting digital assets complex and is why so many aspects of the ‘protection function’ are often outsourced to third-party security providers.
The protection of physical assets, on the other hand, is primarily internal. That is not to say that external parties are not a threat to a company’s physical assets, because they are, in the form of robbery, for example. However, loss of physical assets often occurs internally. Furthermore, the means of protection are more easily accomplished internally for physical assets; for example with physical access controls to certain equipment or machinery on a site. Physical access into a given site or work area is also more easily controlled internally for physical, tangible assets than is the case for digital assets.
Different losses
Any loss is clearly a loss for any organization, whatever nature or extent thereof. However, the loss of a digital asset is invariably a loss of data and, hence, intellectual property. Conversely, a physical asset loss is usually a loss of physical property, i.e. a tangible proprietary loss rather than an intellectual proprietary loss. Furthermore, the retrieval or even replacement of a compromised or lost (read: stolen or hacked) digital asset can often be difficult to do. The replacement of a physical asset is usually possible, even if it can be costly.
Different vulnerabilities
Digital and physical assets are vulnerable in very different ways. Digital assets are often vulnerable from some form of ‘attack,’ often by an unseen digital adversary, as opposed to physical assets that are usually vulnerable to more ‘visible’ factors such as physical theft, whether by internal or external parties, or misuse, for example, machinery used incorrectly by a poorly trained worker.
Furthermore, the single biggest threat to physical assets is that they can be physically compromised, i.e. due to theft or breakage. Digital assets, on the other hand, can be compromised in many different ways, including:
- Data breaches and data losses
- Compromised credentials and confidential company information
- Phishing
- Ransomware as malware
- Unsecured IoT devices and other exploitations thereof
- Cloud storage vulnerabilities
- Distributed denial-of-service (DDoS) and DoS attacks
- Hacked interfaces and insecure application programming interfaces (APIs)
Different protection methods
As the list above shows, there are so many ways in which digital assets can be compromised, making their protection complex and sometimes costly. However, as McKinsey stated in 2017, “Not all systems and data are created equal”. As such, different digital assets will require different protections, with an emphasis on those digital assets considered critical. According to McKinsey, what is important is that top management leads an organization-wide effort to define what are the critical digital assets, and, thereafter, protect them accordingly. In doing so, an organization builds what is referred to as “digital resilience”.
An important way of protecting physical assets is via access control, in which people, be they employees, customers, suppliers, or anyone else with potential access to a site, are physically barred from certain or all access to physical assets. Access control incorporates factors such as authorization or access approvals, multiple identity verifications, and authentications, including others. These controls can also be achieved with Enterprise Asset Management (EAM) software that can help an organization track and manage its physical assets at any time. This can help increase the performance, durability, and viability of physical assets and, ultimately, reduce operational costs.
An important function of an EAM is asset lifecycle management since most physical assets have a discrete lifespan. This approach allows an organization to optimize its physical assets from acquisition to disposal thereof, as seen in the diagram below:
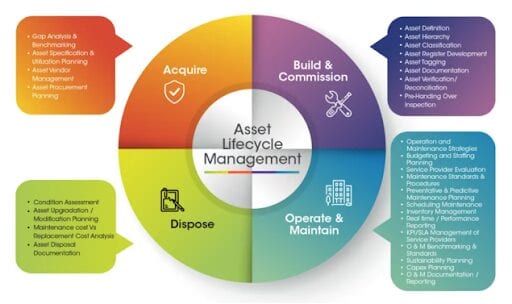
Courtesy: RCA & Company (South Africa)
SIMILARITIES IN PROTECTING DIGITAL & PHYSICAL ASSETS
There are aspects common to the protection of both digital and physical assets, which are worth briefly listing here:
- Comprehensive knowledge (a ‘stock-take’) of all assets, whether physical or digital, is imperative
- All assets need to be risk-assessed within the context of a given and appropriate risk management system
- Both classes of assets require some form of access control and denial as part of their protection
- Regular reviews and audits of all known assets are needed.
Ultimately, all digital and physical assets are business assets, whatever their utility or value. They are hugely important, which is why their protection is so critical for any organization.


