New cybersecurity threats like phishing attacks, ransomware, and scams are always popping up. Stay up to date on the latest widespread threats and protection methods in our recurring series.
FACEBOOK MESSAGING PHISHING SCAM
There is yet another Facebook scam to be on the lookout for. Attackers will pose as connections or use their already-compromised accounts to send messages with content such as “Is this you?” or “What are you doing in this video?”. They will then link to a web address.
Clicking on or typing in the link will lead to malware, infected downloads, or theft of your personal information through phony login pages to a popular service. If they’re able to gather your Facebook login information, they will then continue the scam by sending the same message to your social connections via your account.
What to do: Always think before you click – if your friends wouldn’t normally send a message like this, take the time to confirm with that person through another channel such as phone or email.
If someone is sharing a video with you, you will never have to enter in personal or login information to do so. These scams will often lead you to a phony site where you’re prompted to enter your credentials to see the content.
And always use common sense. Scams like these rely on fake urgency to lower your defenses – there could be something embarrassing in that video, right? Take a second to slow down and think about what you’re doing and scan for common indicators that this is indeed fake.
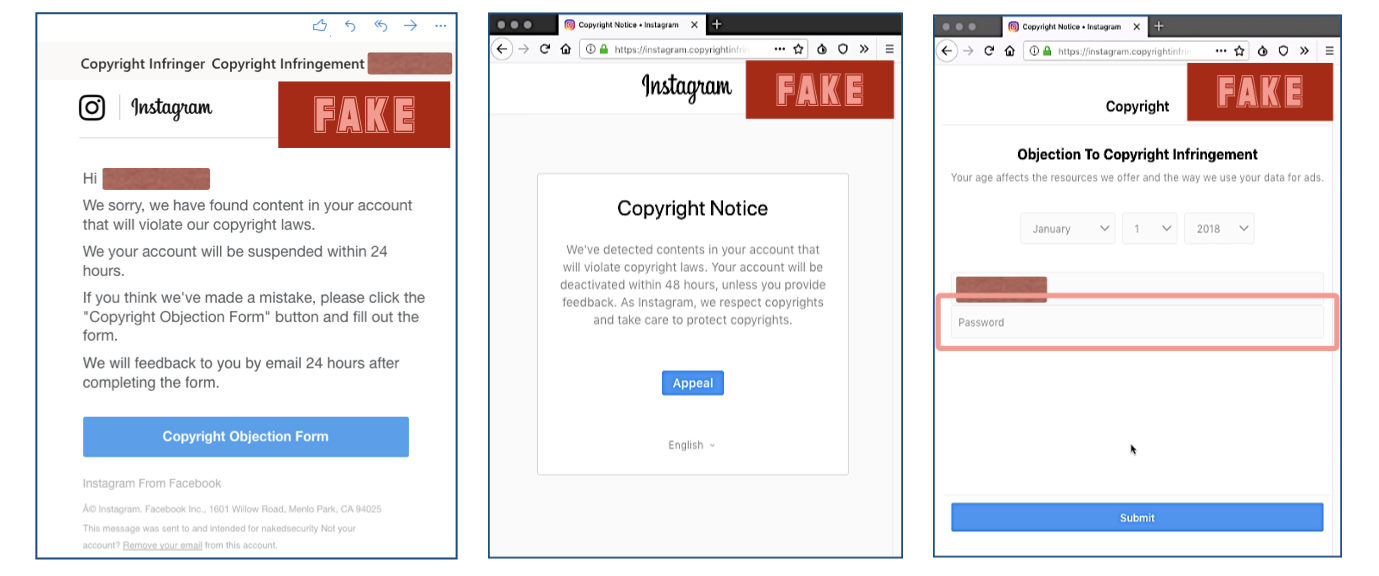
FAKE INSTAGRAM COPYRIGHT NOTICE EMAILS
Instagram users have received emails claiming that their account has been flagged for copyright violations and will have their account suspended within 24 hours if not resolved. The link in the email takes the user to a bogus copyright objection form page that requests their age and account credentials. Filling that in will hand the information over to the scammers.
“The attackers use an instagram.copyrightinfringementappeal.[phishingdomain].cf subdomain (.CF being the country code top-level domain for the Central African Republic) for both the interstitial and the phishing landing page which adds to the illusion that the domain is an Instagram one on mobile web browsers.
Also, the two pages are secured with a valid HTTPS certificate issued by Let’s Encrypt and display green padlocks to further alleviate the users’ doubts that the page they’re on is the real deal. This stands to show that even if you see a green padlock announcing that the connection is secured, checking if the domain is a legitimate one is also a must.
The phishing landing page also displays an age confirmation form probably used to add even more legitimacy to the attack.”
What to do: Stay on the lookout for any emails like this if you’re an Instagram user. There are some telltale signs of a scam – grammar in the email is a bit off, the webpage you’re taken to to submit a claim objection is not instagram.com, and you’re not required to enter any information to refute the claim other than your credentials.
If you’ve had your account compromised or suspect you have, see if you can still access your account. If so, immediately change the password. Doing this will log out any other devices logged in and prevent any further misuse. It’s also a good idea to revoke access to any third-party connected apps. If you’ve been locked out, you’ll need to contact Instagram support for help.
FAKE VETERAN HIRING WEBSITE DISTRIBUTING MALWARE
A fake website attempting to dupe the legitimate hiringourheroes.org was discovered by researchers. The fake website “Hire Military Heroes” prompts visitors to download their free desktop app to use the service. The app is a fake installer that will plant malware on victims’ machines.
What to do: Definitely do not visit the Hire Military Heroes site! You should almost never be asked to install any kind of software to look for job candidates unless it’s a reputable program in your industry. If you haven’t heard of the program, take a minute to do an online search and you’ll quickly find out if it’s legitimate.
BOY SCOUTS OF AMERICA/TRAILS END DATA BREACH
Trails End is the fundraising organization Boy Scouts of America goes through for their popcorn sales. In early September, Trails End notified the Boy Scouts and local councils of “a data incident” picked up by a web developer.
It appears that information including children’s full names, birth dates, email addresses, phone numbers, parent names, product sales, and organization affiliation was visible through a search.
It’s unknown at this time if the information has been accessed or taken by any malicious parties.
What to do: If you or your child is a member of the Boy Scouts of America, we recommend contacting them for updates on this incident and to see if your data was affected.
If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!