New cybersecurity threats like phishing attacks, ransomware, and scams are always popping up. Stay up to date on the latest widespread threats and protection methods in our recurring series.
LINKEDIN PHISHING MESSAGES
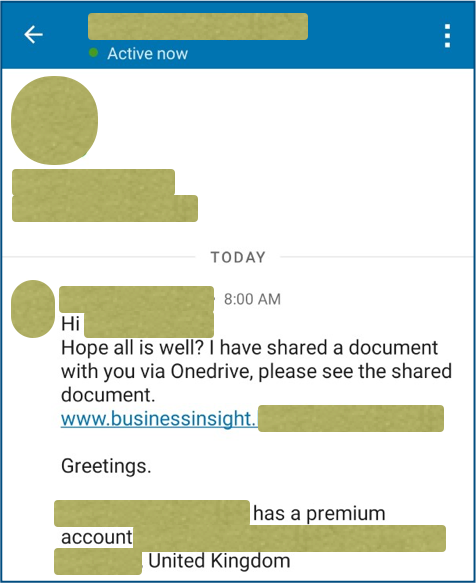
Image via Sophos
Social media accounts are becoming increasingly valuable for cybercriminals. While we expect scams to come through email or phone, we’re less on guard with our social accounts, especially when the attacks appear to come from our connections.
A threat making the rounds currently is through compromised LinkedIn accounts. A criminal will gain access to a profile and begin spamming all of their connections with phishing messages. Some will send malware disguised as a normal file, others will try to steal personal information under the pretense of hiring for work.
While these have been prevalent on Facebook for a while, LinkedIn hasn’t been hit hard until lately. Since it’s more common to conduct business on LinkedIn – sharing work files or hiring for jobs – criminals are realizing they can get away with these scams easily. Compromising one account can help them gain valuable personal and business information on many others.
What to do: If you receive a LinkedIn message asking you to take an action, always be suspicious, especially if it seems out of character for the sender. We recommend contacting them through a different channel if possible, such as a text message, call, or email, to confirm if the message is legitimate. Simply responding to the message on LinkedIn may alert the attacker who can just delete the message or reply themselves.
Also be on the lookout for odd language. Does someone who usually calls you by your first name suddenly use your full name? Or make out-of-character typos? These are usually giveaways.
And of course, to avoid having your account compromised, change your password regularly and don’t reuse the same one across different services.
BUSINESS HR EMAIL SCAM
Image via Tech.co and Kaspersky
This email scam pretends to come from a company’s human resources department. The email asks for users to complete a performance appraisal form. Clicking the included link takes the recipient to a bare-bones online form, which actually works in the scam’s favor as most internal company networks are quite plain.
The form asks the user to sign in with their company email credentials, which are then sent to the scammer. This is disastrous for businesses as the attacker can then access their business email, distributing the scam further, and possibly access other accounts if the person reuses their password on other services (which is extremely common).
What to do: Always double-check if emails like this are legitimate. Since it’s being sent from “your” company’s department, get in touch with the apparent sender through another channel to confirm. If you have an IT person or department, you can also send the email to them to check for any funny business.
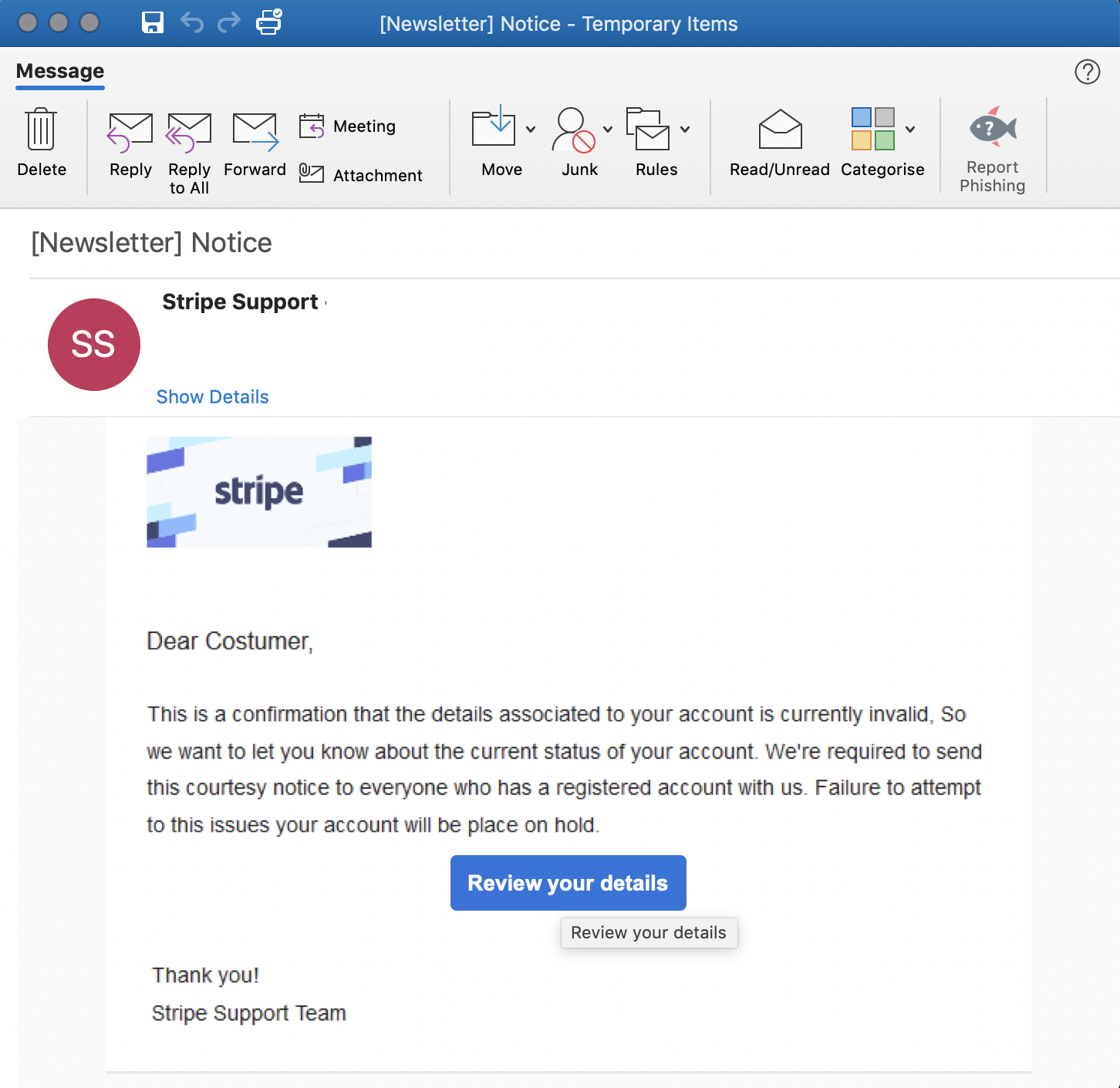
PHISHING ATTACK TARGETING STRIPE USERS
Image via BleepingComputer
Fake Stripe support alerts have been spotted in users’ email accounts. Most of these emails ask the recipient to review details associated with their account. Following the given link leads to a cloned Stripe customer login page where user credentials, bank account numbers, and phone numbers are stolen.
What to do: The fake emails so far are littered with spelling and grammar errors, which is the first obvious giveaway. The URL the link leads to is also not a real Stripe domain. Always be on the lookout for clues like this and be suspicious of any service asking to confirm your credentials or information.
AMAZING WEB SERVICE OVERDUE BILL PHISHING EMAILS

Image via Komando.com
Users and non-users alike of Amazon Web Services are receiving emails that claim their service has been suspended due to an overdue bill. The link included in the email to rectify this takes the recipient to a convincingly realistic page to enter your Amazon account information. Once entered, you’re taken to the real Amazon website, and your credentials are sent to the scammers.
This scam is extra tricky as the email appears quite legitimate and uses the AWS logo along with correct grammar and formatting. The fake account login page uses a URL format that could trick many people – “aws.amazon.com.signin.redirect…” – a true Amazon address would have a ‘/’ after amazon.com to denote it as a subpage, but without looking closely at this address many wouldn’t realize the difference.
What to do: If you receive an email from any service asking you to review or confirm account details, do not follow the link given in the email. Go to the website yourself from your web browser and log in, you’ll be able to view any notifications and see if the email is legitimate.
![]() If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!
If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!