New cybersecurity threats like phishing attacks, ransomware, and scams are always popping up. Stay up to date on the latest widespread threats and protection methods in our recurring series.
INSTAGRAM DATA BREACH

An unprotected Amazon Web Services database containing over 49 million records was discovered exposed online. The data included users’ biodata, profile picture, followers, location, email address, and phone number.
The database was owned and stored online by Indian social media marketing company Chtrbox who has since taken it down. Instagram/Facebook are working with the company to understand how the leak happened, and ensuring their user data is now secured.
What to do: It doesn’t appear as of now that any data was accessed or used maliciously. There were no login credentials or financial details exposed. However, it is always wise to change your password and watch your account for any suspicious activity. Criminals can piece together information from various breaches like this to gather enough details to impersonate you or access other accounts.
BOOST MOBILE DATA BREACH
Boost Mobile announced unauthorized activity on their website in which attackers were able to access accounts. Their statement to affected customers says, “On March 14, 2019, Boost.com experienced unauthorized online account activity in which an unauthorized person accessed your account through your Boost phone number and Boost.com PIN code…The Boost Mobile fraud team discovered the incident and was able to implement a permanent solution to prevent similar unauthorized account activity.”
What to do: Boost has alerted its affected customers and required PIN and password changes. Whether you received this message or not, if you use Boost remember to change your credentials and watch out for fraudulent activity on your account.
WHATSAPP VULNERABILITY
Facebook is in the spotlight in yet another security incident, after discovering that their software WhatsApp contained a remote code execution vulnerability (RCE) being exploited in a targeted attack.
The bug would allow the victim’s device to be infected with spyware simply by being called by the attacker, the victim doesn’t even have to pick up the phone call.
“The firm refused to name who it suspected, saying only that it was the work of an ‘advanced cyber actor,’ that attacks exploiting the flaw had targeted a ‘select number’ of users, and that it bore ‘all the hallmarks’ of a private firm that works with governments to deliver spyware targeting mobiles.” (Infosecurity Magazine)
WhatsApp deployed a fix for this bug soon after it was discovered so it’s not active anymore.
What to do: If you haven’t updated your WhatsApp software since May 10th when the patch was released, do so immediately. If you believe you may have been affected by the spyware, run antivirus/anti-malware scans on your phone and/or take it to a support center to remove any infections.
VOICEMAIL PHISHING SCAM
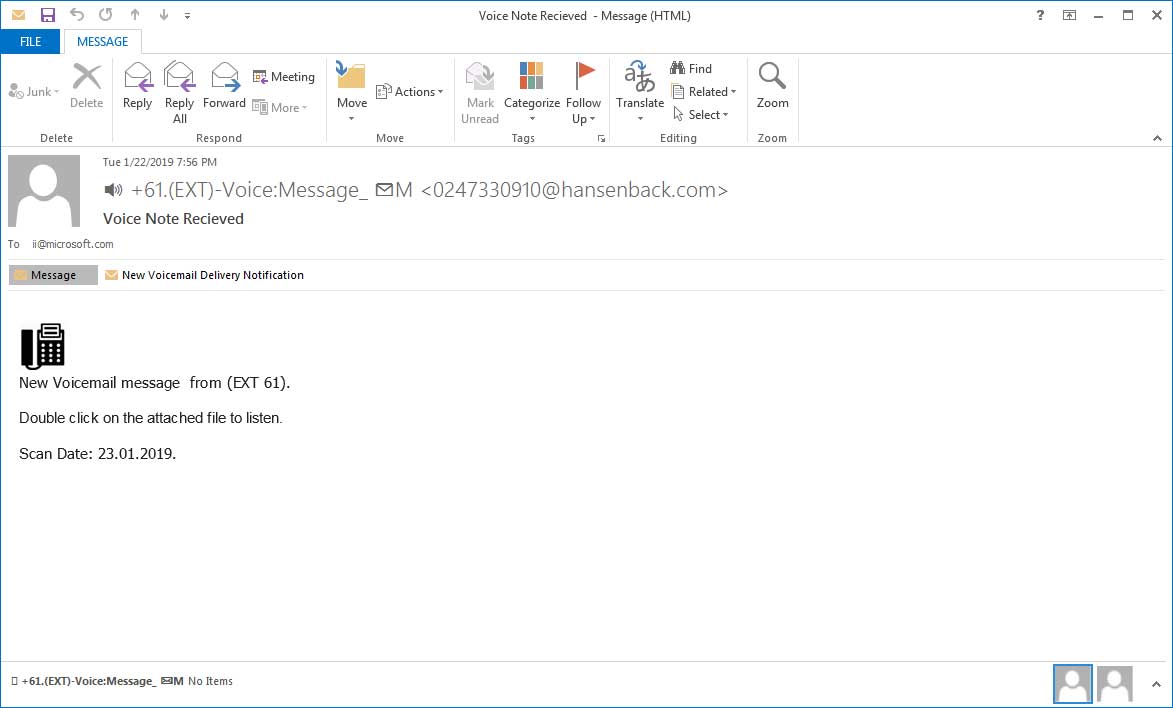
Victims of this scam are receiving emails containing fake voicemail message alerts with malicious links.
“The email looks legitimate, and even contains text claiming the message comes from a ‘trusted source.’ In some versions of the scam, a portion of the voicemail is transcribed in the email. For example, it may say something like, ‘Please contact me ASAP about…’ But when you click on the link, the scammers try to trick you into giving up personal information or downloading malware onto your computer.” (TheIndyChannel.com)
What to do: If you don’t recognize the sender, always be very cautious opening any email attachments or following links. And in this case, you should never have to install or give up personal information to listen to a voicemail! If you’ve been hit and fallen for a scam like this, alert your banks and be on the lookout for any unusual activity.
If you need some extra help identifying or protecting against any of these or other cybersecurity threats, let us know!




