This article first appeared on Contextual Security’s website and is reprinted here in partnership with them.
If you are like me, by now you have experienced firsthand “death-by-virtual-meeting.” With the necessity of online conferencing for business life to continue, we are all well used to the awkward muting and unmuting, talking over each other, and the like.
But what about those “Zoom bombings” you’ve been hearing about? What if someone tries to jump in on your private conference, or worse?
Security vulnerabilities exist in every software created by man. Man is flawed and what man creates is flawed. That means, if there is a man-made computer, there will be some security vulnerability waiting to be discovered.
Two of the most popular business conferencing solutions, Zoom and Cisco Webex, are focused on protecting the privacy of attendee’s conferences, but they aren’t perfect.
ZOOM
Before the global pandemic, Zoom had just begun to establish itself as an industry leader in rock-solid web conferencing for personal, as well as business use. When the stay-at-home orders started rolling out, Zoom was almost chosen unanimously by homes, churches, and even some businesses as the go-to conferencing solution for a stay-at-home economy. Wherever there is an influx in the use of any tool, the bad guys come out of the woodwork to take a peek at what kind of havoc they can cause. When Boris Johnson shared publicly a Zoom meeting ID, he was almost taken advantage of, had his technical team not set up two-factor authentication. Zoom is designed to be used securely, so here are some Zoom Security rules so you can have safe meetings.
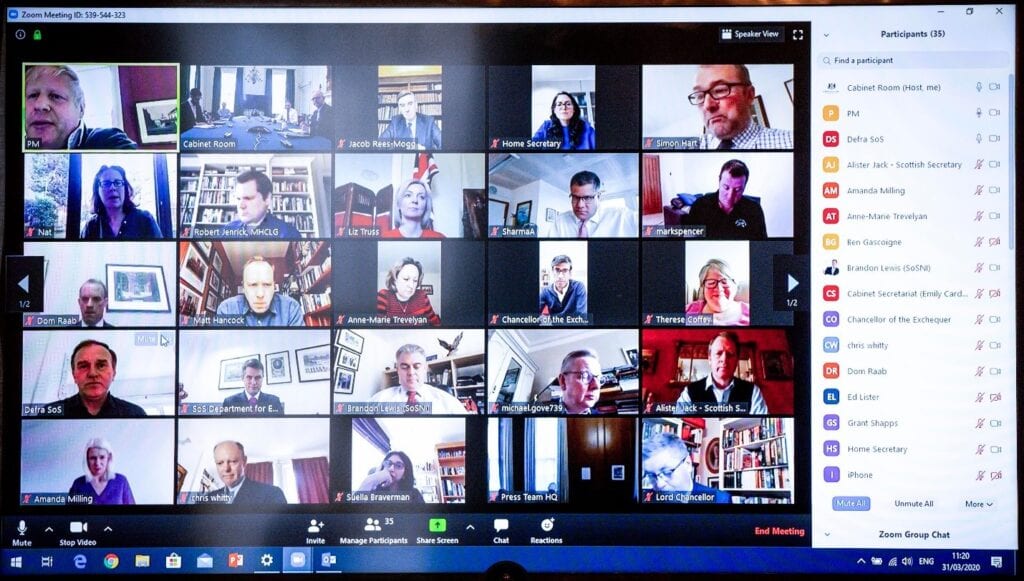
Zoom security configurations
Zoom Security Rule #1: Don’t ever share your Private Message ID (PMI) with anyone you don’t want in your Zoom meeting. Every Zoom user gets a “PMI” and that PMI doesn’t change, so only share it with those you are always willing to have in your Private Meeting Room.
Zoom Security Rule #2: If you are a business, or share sensitive content in your Private Meeting Room, set up Two-Factor Authentication, or at least a password, to keep unwanted guests out.
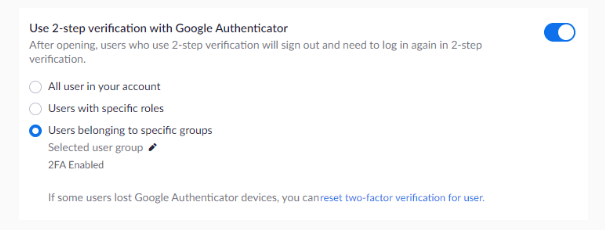
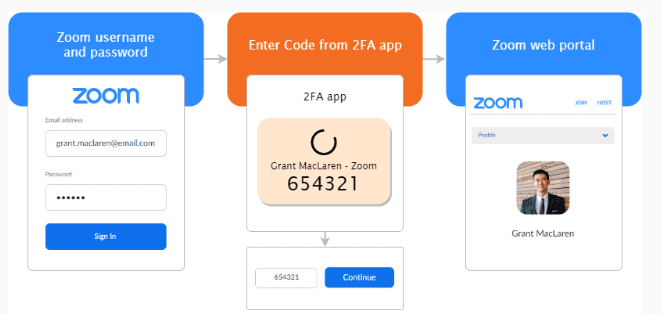
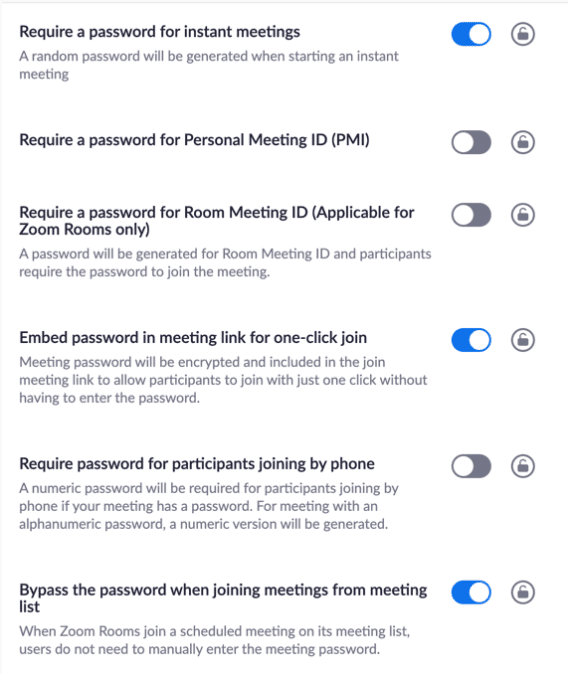
Zoom Security Rule #3: Don’t share your meeting links with anyone you don’t want in your meeting. Since the meeting links will allow anyone to join who clicks the link, without password protection or multifactor authentication, your meeting is open to everyone.
Zoom Security Rule #4: Know Zoom security and meeting management configurations. Knowing how you can dial in your Zoom meeting configurations is critical to making Zoom work for your organization. From locking out screen sharing to auto-muting participants, knowing Zoom will build security and efficiency into your meeting processes.
Zoom vulnerabilities
In general, Zoom has done a terrific job getting ahead on security. From repeated emails to customers about security updates, to feature releases almost weekly, Zoom is taking a stand to say that they care about the security of their clients. However, vulnerabilities and exploits are already in the wild. Here are some of the highlights:
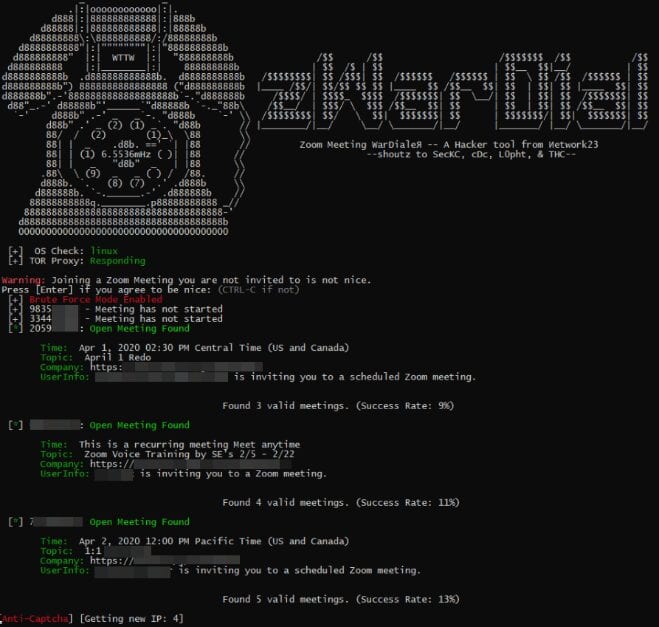
Zoom Vulnerability #1: As detailed by this Krebs article, an exploit is already in the wild taking advantage of Zoom’s default configurations. Imagine taking war dialing, the practice of dialing around with specific software and phone equipment to find insecure lines, and turning it into an online web conferencing attack platform. That’s exactly why understanding clearly the security settings of Zoom meetings is critical to making sure you aren’t open to tools that can exploit the way Zoom was designed to work.
Zoom Vulnerability #2: As detailed in this Tweet from @hackerfantastic, Zoom locally passes credentials in Windows (and Mac, as detailed down the reply thread) in such a way that the credentials can actually be captured, cracked, and reused in man-in-the-middle attacks. While this won’t allow further access to Zoom in particular, it can allow credential disclosure and subsequent Windows privilege escalation if not dealt with.


Zoom Vulnerability #3: This blog outlines a Zoom security vulnerability for Mac OS that allows webcam hijacking. While it is patched as of this writing, users who are on Mac OS should make sure they are on the latest patched version. Organizations that use Mac OS should confirm patch levels for all devices.
Zoom Vulnerability #4: This vulnerability is specific to Linux distributions of Zoom, which seem to be quite behind the curve of Microsoft and Apple’s Zoom offerings. So far, no major replies have been offered to the tweet as of this writing. Zoom Linux users beware, for now.
While Zoom has a great deal of rapid-growth issues, from scaling their infrastructure to security vulnerabilities, it’s not all bad. Many security researchers, as detailed in the links above, have reported Zoom to be responsive, quick at patching, and concerned about the security posture of their product. In short, don’t lose confidence in Zoom, but be aware, get patched, and know your product.
CISCO WEBEX
While Cisco Webex is nowhere near the household name as Zoom is, they are trying to market themselves as such. Designed primarily as a business conferencing solution, Cisco has upgraded their free plan to make Webex a free tool for up to 100 users and with unlimited time on meetings for an indefinite period of time, presumably for the duration of the stay-at-home orders. Webex is just as fast, crisp, and reliable as Zoom, and backed by a company that has large coffers and years of success at making it a solid product.
Cisco security configurations
Cisco has provided a comprehensive guide to securing Webex. It’s very similar to that offered by Zoom above, but you can click here for more information.

Cisco vulnerabilities
Cisco recently rid themselves of two particularly bad security vulnerabilities last month. However, since both vulnerabilities deal with an unauthenticated attacker’s ability to execute remote code, users of Webex should confirm they are on the latest patched release.
CONCLUSION
Whichever solution you choose (or a different one altogether), your success is not as dependent on the solution, but on knowing the tool, properly configuring the tool, and staying up-to-date with the latest vulnerabilities of the tool.




