At Techvera, we perform countless virus/malware removals every week. The question our customers always ask is how they can avoid reinfecting their computers in the future.
There are an estimated 70,000 new instances of malware and viruses released per day, and the creators are becoming more and more clever at tricking you into infecting your computer. It can be difficult to spot and avoid attacks, but arming yourself with the right tools and knowledge will greatly reduce your risk.
Here we present some common infection methods and scams to help keep you as protected as possible and different removal tools for when something makes it through.
HOW MALWARE, ADWARE, AND SPYWARE GET ONTO YOUR COMPUTER
“First, let’s take a look at the ways users commonly become infected. Malware, spyware, and other junk software make it onto your computer for a number of reasons:
- You installed something you really shouldn’t have, from an untrustworthy source. Often these include screen savers, toolbars, or torrents that you didn’t scan for viruses.
- You didn’t pay attention when installing a ‘reputable’ application that bundles ‘optional’ junkware
- You’ve already managed to get yourself infected, and the malware installs even more malware
- You aren’t using a quality antivirus or anti-spyware application”
Deceptive installers
One of the most frequently overlooked ways that junk makes it onto your computer is through reason number two above: you were installing software from a reputable company, but that company decided to profit by packaging its program with unwanted toolbars, games, etc.
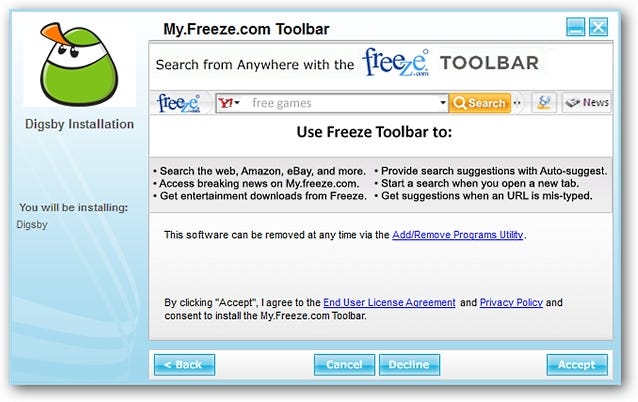
This is a deceptive practice, and often the installer makes it look as though you simply can’t finish the installation without approving the unwanted applications. This page via howtogeek.com outlines a great example using the Digsby Messenger program.
“You can see the attempt to add the ‘My.Freeze.com Toolbar’ to your browser(s)…definitely not good! Notice that while it does state that the software may be removed later, some people may 1.) Not notice it (lack of attention), 2.) Be in too much of a hurry to install the software to notice, or 3.) Not be familiar or comfortable with removing the software after it is already installed on their system.
The real trick with Digsby (and other software that is set up with the same installation style) is that clicking on ‘Decline’ still allows the installation of Digsby itself to proceed. But can you imagine how things can end up for those people who may think or believe that the only way to get Digsby or similar software installed is to click on ‘Accept’? It has a really deceptive style!
If you have many programs that attempt to install ‘value-added’ software like this on your system, you will quickly find that the majority (or all) of your operating system’s resources are being used up by malware (i.e. background processes). You are also likely to find that you will have unstable or very sluggish browser response, and are likely to have your personal and computer’s security compromised.“
This same Digsby installer also attempts to change your browser’s homepage to the my.freeze.com site, another common trick throughout many installer programs. This can also be safely declined without preventing the Digsby Messenger install, but you can see how this is not completely clear to the user.
Moral of the story: be alert throughout software installations, and say NO to unnecessary, sneaky adware/malware/spyware.
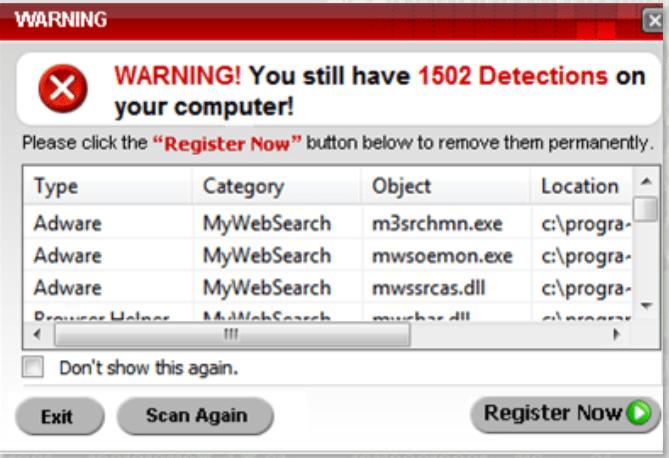
“Scareware” and fake antivirus programs
Scareware is a term for software that will attempt to trick you into believing that your computer is full of infections. These programs will pop up (sometimes constantly) telling you to register and pay for the software to take care of these thousands of “infections”.
Many of these programs are designed to look as legitimate as possible and can be hard to tell apart from the real deal. However, no legitimate antivirus program will pop up out of nowhere and use big, flashy, scary words and icons. This is why it is called scareware, it will use bold wording and flashy graphics to try and scare you into both installing malware onto your computer and giving the creator your hard-earned money!
Furthermore, upon close inspection, many of these notifications/programs will be rife with broken English, out-of-place punctuation or capitalization, and/or spelling errors, something a reputable antivirus program would never let through.
If a program looks at all suspicious, it probably is! If you have never seen the program before and it is telling you detailed information about your computer, that is a red flag.
If you’re ever in doubt, a quick Google search of the name of the software in question should give you an answer. Users will flock to the internet to expose scams, and you will often see stories of people who have been fooled by the software, and countless pages with instructions on how to remove the program from your system. If all you can find is negative feedback and websites describing the program as malware, then you can be sure it is a fake.
Another increasingly common version of this scareware tactic has become known as the fake tech support scam. A popup will appear on your computer claiming to be coming from a well-known corporation such as Microsoft, HP, Google, etc. It will alert you that your computer is infected, full of errors, or encountering some other issue and to call a number displayed on the screen for immediate help. It will often warn you against even shutting down or restarting your computer.
This is all a scam – Microsoft and other corporations do not have the manpower nor the desire to keep track of every single user of their software and their computer’s health; it would take thousands upon thousands of employees dedicated solely to this task to even be remotely feasible. These messages are always from scammers, who will trick you into letting them remotely log into your machine to steal information, plant malware, and take whatever money you are willing to give them while fixing nothing.
Never let one of these scammers into your computer and never give them your money!
Fake download buttons
Take a look at this picture:
Can you spot the real download? Oftentimes you will be attempting to download a legitimate program or file, but the page is littered with fake and misleading download buttons. These will just about always lead to a malicious website, annoying popups and advertisements, or installing unwanted software/malware. These are specifically designed to confuse you into clicking a fake/unwanted link.
A few tricks you can use to weed out the impostors:
- Look out for fine print either above or below the button that says “advertisement”. Likewise, look around the button in question to see if it indicates that it is related to a different program/website.
- Notice the little blue arrow in the top right corner of many download buttons. These indicate a redirect to a different website – not the download you are looking for.
- Most sites will not even use download buttons like these ones. Oftentimes, the correct download will be the least eye-catching!
Taking just a minute to examine and think before you download or say yes to anything can save you time, money, and heartache down the road.
Free games, applications, and screen savers
Many free applications and games are simply vehicles designed to install malware. Even if the application itself seems to work the way you expect, malware may still be installed on your computer. Oftentimes you will notice those rogue toolbars, popups, and applications you didn’t intend to install appearing on your computer. Only download applications from trusted websites to help avoid this.
Media players
“A popular source of malware is a website media player download. When a user wants to play a video, the website will ask to install a video codec or other required software. When the user installs the application, the malware is also installed and the video may or may not play. No matter how enticing the video, only install media player software from trusted websites such as Apple.com, Microsoft.com, and Adobe.com, winamp.com, videolan.org.”
Malicious video player popups will often display a source or “logo” that is similar to a reputable company but with some sneaky differences. Whenever something like this pops up on your screen, validate that the source it is coming from is the actual company, not an impostor. If you still aren’t sure, go directly to the company website and download the needed plug-in/codec straight from them, not from the popup prompt.
Email attachments and phishing emails
One of the oldest and most frequent ways to spread malware is through bogus email attachments and “phishing” attempts. Email attachments can come from anyone, and will often look like they were sent by someone you know if their email account has been compromised.
To avoid infecting your computer this way:
- Do not open attachments from people you do not know
- If a friend sends you an attachment that looks suspicious contact them first before opening the attachment
- Never open email attachments that end in .exe, .bat, .com, .vbs
Phishing emails will try to convince you to click a link within the email, taking you to a website that will either install malware or steal your personal information under the guise of a business you use frequently (banking, online retailer, subscriptions, etc). The majority of companies have rules against ever asking you for personal information through your email account. 99.9% of the time, even if the email looks to be coming from a company you are familiar with, these emails will be scams.
You will often notice that the sender’s address will mimic the actual company’s webpage address, but with a slight difference, or will be from a completely random and unrelated email address (notice in the examples above). Never click on links contained in these emails or enter any of your personal information, and if you are ever in doubt contact the company directly to confirm or deny your suspicions.
HOW TO REMOVE MALWARE FROM YOUR COMPUTER
Now that we know the common ways computers can become infected, how can you remove malware and unwanted applications? There are a few great, trustworthy, and free programs to help you rid your computer of junk. If malware/viruses are blocking your removal tools or just aren’t able to remove everything, it is always recommended to take your computer to a professional repair place. IT support companies have multiple tools and utilities to remove every trace of malware and viruses safely.
The program that we use and recommend most often is MalwareBytes Anti-Malware. It is one of the most powerful malware removal tools, and is very user-friendly. However, it is only a removal tool designed to work alongside your current antivirus. The free version does not offer real-time protection and can’t prevent or thwart incoming attacks, so it is a good idea to run it on a weekly basis, or as needed. Real-time protection is offered in the paid version if you like the software and decide you need an extra level of protection. The free version is more than sufficient in its removal capability, however.
Download MalwareBytes Anti-Malware here
Ad-Aware Free Antivirus+ by Lavasoft is a trusted spyware/malware tool and has been a popular program for many years due to its smooth and easy installation, non-intrusive nature, and comprehensive removal. The free version does provide real-time antivirus and malware protection. While it is a bit lacking in its anti-phishing and rootkit protection, it is still a great program for the $0 price tag.
Download Ad-Aware Free Antivirus+ here
A feature-rich and popular program is avast! Free Antivirus. Aside from the usual virus and malware protection, it offers anti-rootkit and anti-spyware capabilities, a slew of customization options, and even remote capabilities. The interface is clean and user-friendly; most new users can find their way around easily. The only major headache with avast! is that is has a tendency to incorrectly label valid programs as possible malware, which can be a bit of a pain. But again, for the price of free, avast! is a great application.
Download avast! Free Antivirus here
While there are a vast amount of free antivirus and anti-malware programs on the market, just about any user can find software they like within these three applications. Even after removing the offending software, you may notice that your browser settings will still need to be changed manually if they were affected by malware. Here is a great guide on how to fix browser settings changed by malware that covers Internet Explorer, Mozilla Firefox, and Google Chrome. If your homepage was changed, toolbars or extensions were added, or websites redirect elsewhere you will want to check out the guide.